FunkSec
The Fragile Face of AI-Generated Ransomware

By Riyad Jazmawi
Head of Information Security and IT Governance, INVESTBANK
FunkSec emerged in late 2024 as a fast-moving Ransomware-as-a-Service (RaaS) family that quickly drew attention for its combination of modern tooling and obvious implementation weaknesses. FunkSec is a Rust-based ransomware, meaning it is developed using Rust instead of traditional languages like C and C++. The ransomware employs a double-extortion approach, encrypting victims’ files while exfiltrating data for public shaming. The family demonstrated how new development workflows (including the use of generative AI to write large portions of code) can accelerate an actor’s reach while also introducing mistakes. The result is a strain that is capable and dangerous in the hands of affiliates, yet flawed enough that defenders have repeatedly found practical openings for detection and recovery.

A recurring theme in public analyses is FunkSec’s reliance on AI-assisted code generation. Using large language models enabled affiliates with limited programming experience to quickly produce ransomware, but LLMs tend to generate plausible-looking code without guaranteeing robust error management. This lack of rigorous testing is evident across FunkSec builds, manifesting as logical assumptions and fragile control flows that fail under real-world conditions. Rather than mature, well-engineered malware, many FunkSec samples resemble a rapid prototype: functional, but fragile.
One clear manifestation of these problems is FunkSec’s drive enumeration logic. Several samples treat every mounted volume as if it were removable media, copying themselves to each detected drive and failing to differentiate between fixed system disks, network shares, and actual USB devices. This misuse of drive semantics leads to inefficient scanning and, in some cases, skipped targets; it also produces unusual API usage patterns that defenders can monitor. Proper use of standard OS calls (for example, querying drive type using the Windows API GetDriveType) would have avoided these mistakes, but the AI-generated code often overlooked these capabilities.
Another operational mistake that surfaced in multiple reports is a dependency on downloading and setting a ransom wallpaper. Many FunkSec variants attempt to fetch an image from a remote server and apply it as the desktop background. If the download fails due to network filtering, a dead URL, or an HTTP error, the encryption routine can crash instead of continuing. Tying a core destructive action to a cosmetic operation is poor logic. It has given defenders a straightforward mitigation: blocking the wallpaper URL or otherwise disrupting an auxiliary step can sometimes prevent encryption from completing.

The ransomware has revealed another vulnerability due to the reuse of default artifacts. Analysts observed connections in some builds to local IP addresses on port 4444, the default Metasploit port for a reverse shell. Seeing traffic to 4444 is a classic indicator of a Metasploit-derived payload, suggesting the reuse of common templates and a lack of operational sophistication in choosing stealthier or customized communication channels. Whether present in all samples or only some, the presence of such defaults is an operational weakness.
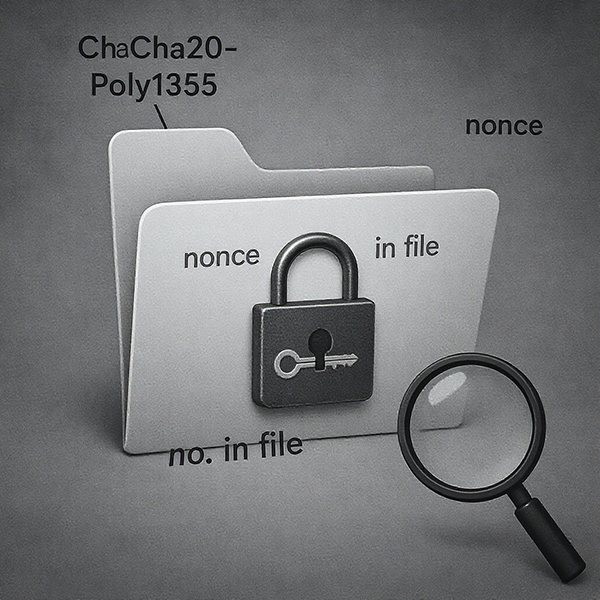
Cryptographic implementation is where FunkSec demonstrates both modern choices and significant mistakes. Many variants use ChaCha20-Poly1305 (and some analysts report XChaCha20 in some variants) implemented via Rust crypto libraries, which, in principle, are strong primitives. However, poor key and nonce handling in certain builds, combined with inconsistent design decisions across variants, undermined the intended security. For example, in some cases, the malware stores the nonces or even key material directly into each encrypted file in ways that made recovery easy for researchers. Rather than properly wrapping cryptographic material in a protected header (for example, encrypting it with an RSA key), flawed implementations enabled security vendors to produce working decryptors.
FunkSec’s process and service termination routines further illustrate the trade-offs of automated coding. The binary typically contains a hardcoded list of processes and services to stop, such as browsers, mail clients, backup tools, and security services, intended to free file handles and disable protections. While this is a common ransomware tactic, FunkSec’s lists are overbroad and sometimes redundant. The noisy, large-scale termination behavior creates high-confidence detection signals (i.e., mass process kills followed by bulk file I/O).

Taken together, these flaws paint a consistent picture: GenAI enabled rapid development and wide dissemination of FunkSec, but they also introduced fragile logic, improper error handling within the malware workflow, and insecure cryptographic practices. For the security team, the very mistakes FunkSec exhibits – failed wallpaper downloads, drive misclassification, default C2 ports, recoverable key material, and mass process termination – are practical signals that incident responders can use for detecting, preventing, and containing AI-powered malware.
The broader takeaway is that while GenAI may accelerate the speed with which ransomware families like FunkSec spread, it does not necessarily translate into greater sophistication. Training security analysts to spot these GenAI coding indicators not only helps identify FunkSec variants but also prepares security teams for the next wave of AI-assisted malware, which will likely share the same strengths and weaknesses.
























