Red Teaming
Red teaming is the art of practicing cyber-operations attacks against a given target from an adversarial point of view to, improve the security posture of the target organization, and continuously increase the resilience of an organization against sophisticated attacks. A particular group focuses on training and developing their skills to avoid failures and acquire self-awareness, reflection, and critical thinking. These failures are usually repeated, so Red teams are there to prevent them from occurring.
Red teaming utilizes techniques that involve a cyber exercise, human attacks, and/or physical attacks, however, the main goal behind it is to identify weaknesses, find areas to improve, and implement effective security measures.
The Red Teaming core elements could be one of the following:
The objectives of Red Teaming can vary depending on the goals of the organization, includes (not limited to)
Red teaming can help organizations determine how well their security controls are functioning by attempting to bypass them.
Red teaming exercises can be used to provide realistic training for security personnel, allowing them to practice responding to real-world threats.
Many regulatory standards including but not limited to HIPAA, PCI, and FFIEC define penetration testing methodologies. Although we believe that penetration testing and red teaming differs in many areas, IT Security C&T Red Teaming methodology was inspired and aligned with the Penetration Testing Execution Standard (PTES) and the National Institute of Standards and Technology (NIST) Special Publication 800-115.
IT Security C&T considers Red Teaming Operations as a realistic approach to security testing. It goes beyond vulnerability assessment and penetration testing, as it takes in scope elements within the organization and applies realistic scenarios-based approach against those. Each attack scenario has a tangible objective aligned and adapted to the customer needs. Red Teaming Operations help to evaluate threats, protect critical assets and respond appropriately to real attacks.
Effective testing often involves launching attacks on real systems using the same tools and techniques being employed by today’s malicious threat actors, to include:
Objective-Led Red Teaming
We believe that Red Teaming is not scope based approach like any Penetration testing project. One of the types of Red teaming is to orient it as Objective-Led project. In this situation, technical interviews with the customers are performed, from which threat profiles are chosen for mimicking those within the environment. One of the examples are: Reaching ERP system, Stealing research information, access CFO/CEO laptop or office, etc.
Training-Led Red Teaming
With this type of Red Teaming, interactive sessions are conducted between blue and red teamers, where the goal is to let the blue team experiment with the different attack exercises which will allow them to improve their detection capabilities, enhance reactions, and minimize the DWELL time and so the response time of incidents.
Threat Intelligence-Led Red Teaming
With this type of Red Teaming, both Threat Intelligence and Red Team providers collaborate with each other’s to achieve a tangible objective. The Threat Intelligence provider produces a Targeted Threat Intelligence (TTI) report for the entity and setting up threat scenarios for the tests. The Red Team provider uses the produced TTI report to develop attack scenarios and execute intelligence-led Red Team tests.
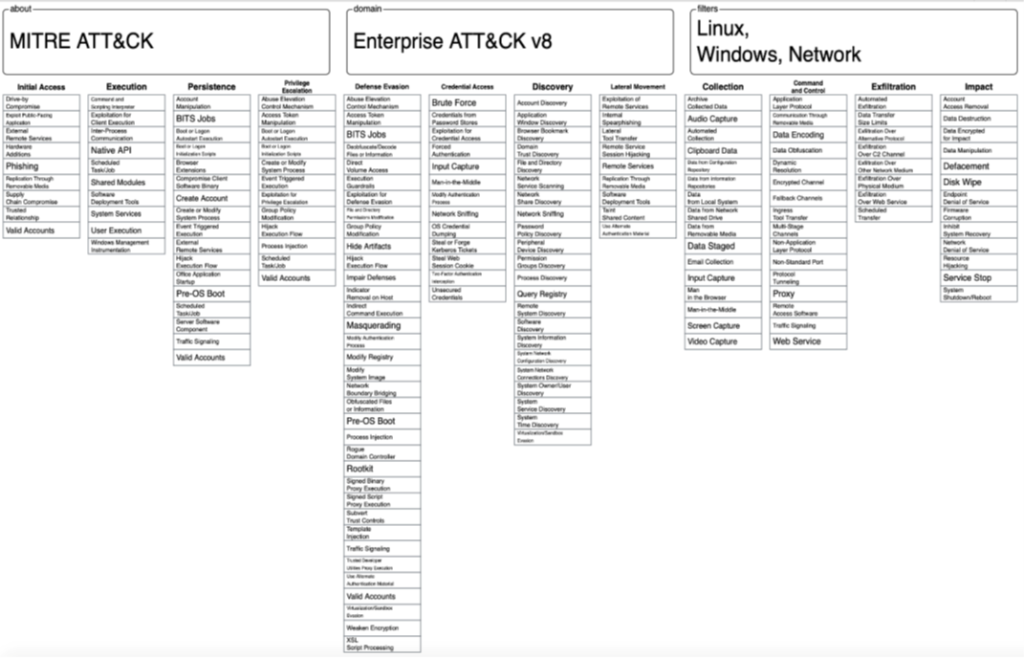
TOOLS and MITRE ATT&CK framework
All the attacks during the engagement will be conducted based on the MITRE ATT&CK framework. The framework lists – in a very detailed manner – each TACTIC, TECHNIQUE and the TOOL(s) used during an attack phase. The tactics are chosen based on the phase labeled as “Choosing a Threat Profile” in the coming table that describes the engagement PHASES mentioned in following section. The benefit behind using these tools is to improve the detection capabilities of the SOC team. Additionally, IT Security C&T consultants use commercial tools to achieve some other goals and among those:
• Burp Suite Pro
• Acunetix
• CobaltStrike
• Etc.
Figure - MITRE ATT&CK Framework
The deliverables of a red teaming service typically include:
Detailed Report
A comprehensive report that summarizes the findings of the red teaming assessment and provides recommendations for improving the target organization’s security posture. The report typically includes a description of the methods used, the vulnerabilities and exploits identified, and any other relevant information.
Presentation
A presentation that summarizes the key findings of the red teaming assessment and provides recommendations for improving the target organization’s security posture. The presentation is usually delivered to senior management and other stakeholders.
Recommendations and Action Plan
A set of recommendations and an action plan for improving the target organization’s security posture. The recommendations are based on the vulnerabilities and exploits identified during the red teaming assessment.
These deliverables provide organizations with valuable insights into their security posture and help them to improve their overall security and resilience in the face of evolving threats. They also help organizations to maintain a culture of continuous improvement and security-consciousness, and provide a baseline for regular assessments to ensure that the security posture remains strong and resilient over time.