Red Teaming in Action
In cybersecurity, “red teaming” refers to a form of ethical hacking that is objective-driven and focused on specific goals, without causing any damage to the targeted environment.
- What are the Differences Between Penetration Testing and Red Teaming?
- Benefits of Red Teaming
- Methodology and Approach
- Assessment - Tools
- Used Frameworks
- Sample of Red Team Scenarios

This is achieved through various techniques, including social engineering, physical security testing, and ethical hacking, to imitate the actions and behaviors of a real attacker who employs a mix of different cyber attackers' tactics, techniques, and procedures that may initially seem unrelated but ultimately enable the attacker to reach their objectives.
The goal of red teaming is to give organizations valuable insights into their cybersecurity defenses by identifying gaps and weaknesses that need attention. By simulating real-world attackers, red teaming helps organizations understand how their systems and networks could be exploited and offers a chance to reinforce their defenses before an actual attack takes place.
What are the Differences Between Penetration Testing and Red Teaming?
However, it is important to highlight that Red Teaming and Penetration Testing are not opposites but rather complement one another. Penetration Testing is especially effective for evaluating the security of new applications, features, or infrastructures prior to deployment, whereas Red Teaming is advisable for assessing an organization’s overall security maturity.
Benefits of Red Teaming
Red Teaming is a valuable tool for organizations of all sizes. There are several key benefits to using a red team activity :
(Click on each benefit to read more)
A red team offers an objective view on a business plan by identifying flaws and weaknesses often missed by those involved in the planning.
A red team helps uncover hidden risks and vulnerabilities, especially in complex or high-stakes situations, allowing organizations to address them before they cause problems.
A red team encourages healthy debate by challenging plans and decisions, sparking new ideas and critical thinking. This promotes a culture of continuous improvement and better decision-making within the organization.
A red team helps organizations build resilience by exposing them to diverse viewpoints and scenarios, improving readiness for unexpected challenges and reducing cyber breach risks.
However, red teaming can be time-consuming, and may face internal resistance. To address this, organizations should secure resources, set clear goals, communicate its benefits, and ensure exercises are controlled and ethical.
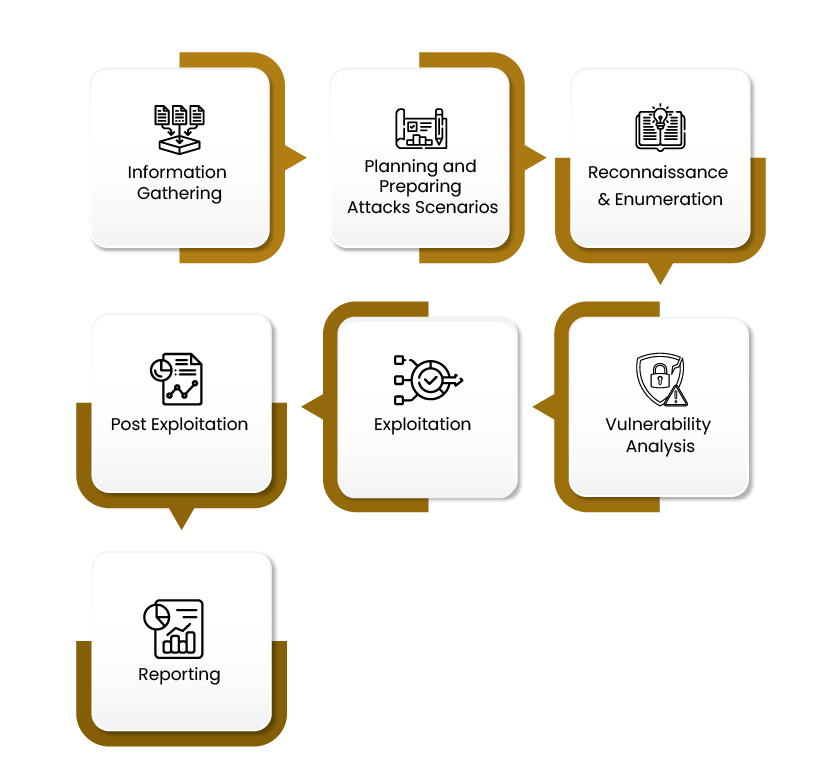
Methodology and Approach
The following represents the phases that will be followed in conducting the red teaming exercise:
However, it is important to highlight that Red Teaming and Penetration Testing are not opposites but rather complement one another. Penetration Testing is especially effective for evaluating the security of new applications, features, or infrastructures prior to deployment, whereas Red Teaming is advisable for assessing an organization’s overall security maturity.
(Click on each phase to read more)
In this phase; multiple workshops will be conducted with the customer to understand what kind of attacks they would like to simulate against their environment and agree on the objectives of the assessment.
In this phase, the consultants will start preparing all the attacks that will be simulating against the environment based on the agreed objectives in information gathering phase. Moreover, all the tools that will be utilized in each attack will be defined along with the execution timeline for each attack. The following represent an example of what kind of attacks can be performed during the assessment:
In this phase; the consultants will start gathering all the information related to the prepared attacks from different sources such as but not limited to network topology, external services, external IP addresses, the web applications, the mobile applications, subdomains, wireless networks, users, clients and much more.
In this phase; the consultants will start analyzing all the assets identified in the previous phase to detect any potential weakness that could be exploited by cyber attacker to get into the network and systems.
In this phase; the consultants will try to exploit the identified vulnerabilities and get into the network to evaluate what kind of information the cyber attacker can obtain after exploiting those vulnerabilities.
During this phase the team aims to complete the mission and realize the agreed-upon objectives set by the client and the consultants. Actions on objective happen through lateral movement throughout the cyber environment as well as the physical facilities. Ultimately, the team aims to achieve the agreed-upon goal which could be to exfiltrate data, information, or physical assets you deem critically sensitive.
In this phase; the consultants will develop a detailed report that highlights all the attacks that have been simulated against the environment along with the results of each attack with set of recommendations that should be implemented to improve the overall security posture of the client and ensure that this kind of attacks will never affect the client.
Assessment - Tools
During a Red Team, a number of tools can be used to achieve the defined objectives. These tools include (but are not limited to) :
Shell
programs designed to execute instructions given by a command-and-control server (called C2) on an infected machine. These implants can also enable the Red Team to use the infected machine as a bounce point to an internal network.

Password spraying tools (Brute force)
for testing common password combinations against multiple user accounts.

Scanning tools
to discover assets exposed on the Internet and known vulnerabilities.

Phishing utilities
open-source frameworks designed to simulate real-world phishing attacks for security awareness training and red team assessments. They allow testers to craft custom emails, landing pages, and track user interactions such as link clicks and credential submissions. These tools help organizations measure human vulnerabilities and improve their phishing defenses.

Used Frameworks
In Red Team cybersecurity activities, several frameworks are commonly used to structure, guide, and execute offensive security operations effectively and in alignment with known attack methodologies. These frameworks cover tactics, techniques, procedures (TTPs), toolsets, and even compliance/engagement planning. Here is a summary of the most widely used ones:
| Framework | Focus | Best For |
|---|---|---|
| MITRE ATT&CK | TTPs of real-world attacks | Mapping/red team simulation/reporting |
| Kill Chain | Attack lifecycle | Planning/testing defense-in-depth |
| NIST SP 800-115 | Technical assessment methodology | Formal engagements, compliance |
| CBEST / TIBER-EU | Threat-led testing (Finance) | Regulatory/government sectors |
| OSSTMM | General security testing | Multi-layer red team testing |
| PTES | Pen test methodology | Full red team planning and execution |
Sample of Red Team Scenarios
Microsoft Active Directory
When it comes to large enterprise environments, it is necessary to manage computers, networks, users, groups, etc.. in a centralized manner. Active Directory is the need of the hour where it caters to the same, perhaps, it comes with its own drawbacks if not configured securely. Red Teaming Against Active Directory comes to measuring the security posture of the overall AD infrastructure and to find out if an attacker can find a way to a domain administrator inside an organization’s network.

Attack Description
When it comes to large enterprise environments, it is necessary to manage computers, networks, users, groups, etc.. in a centralized manner. Active Directory is the need of the hour where it caters to the same, perhaps, it comes with its own drawbacks if not configured securely. Red Teaming Against Active Directory comes to measuring the security posture of the overall AD infrastructure and to find out if an attacker can find a way to a domain administrator inside an organization’s network.
The following represents the steps that we can follow to perform this kind of attacks:
- We can enumerate useful information from AD environment.
- Analyze the collected information to identify the shortest path that allows the insider threat from escalating the privileges to a domain admin privileges (utilizing our PT account).
- Kerberos Attacks.
- Abusing Cross Forest Trusts.
- Delegation Issues.
- Abusing SQL Server Trusts in an AD Environment.
- Bypassing Defenses.
Attack Objectives
The following represents the objectives of this attack:
- Assess the security level of the deployed endpoint security controls to verify if they are going to block our scripts that will be utilized in this attack.
- Assess the current configurations of the deployed active directory.
- Escalating normal AD account privileges to DA account.
Assess the security level of the deployed network security controls if they are going to block our attempts while communicating with the deployed active directory.
Social Engineering
Social engineering is the art of manipulating people to either get sensitive and confidential information about the target which shouldn’t be disclosed or compromise the human weaknesses to gain access to the internal environment. This attack could be conducted using multiple methods such as Emails, Phones, Physical Access, etc

Attack Description
In this attack, we can install a fake advertisement on HQ premise that has QR code to check if any of the employees will scan this QR code; once the QR code is scanned, the mobile phone will be redirected to a phishing page similar to the SSO application of the company and ask the users to insert their username and passwords, after that, all the provided usernames and passwords will be sent to one of our servers and verify if any of those accounts has VPN access to the network or not.
The following represents the steps that we will follow to perform this kind of attacks:
- Develop an advertisement that has a QR code which will redirect the users to phishing link similar to the company Login page.
- Ask the users to insert their domain email address along with their password.
- Once we have a list of compromised users; we will start verifying if any of those accounts have VPN access to the network.
- Try to access the email addresses of the compromised users to evaluate if we are going to obtain sensitive information about the company and its main projects.
Attack Objectives
The following represents the objectives of this attack:
- Assess the awareness level of the employees and evaluate how do they respond in case they are being in a situation that might enforce them to share sensitive information.
- Assess the security level of the deployed physical security controls to verify if it is going to detect our malicious QR code.
- Assess the security level of the VPN.
Wireless Network Attacks
The objective of this test aims to evaluate the security level of the wireless network and to assess if any malicious attacker can compromise the organization by exploiting wireless network weaknesses.
The assessment will consist of rounds between the offices to discover the SSIDs configured and any hidden SSIDs, then we can assess the security level of the client authentication.

Attack Description
In this attack, we can assess the security level of the configured wireless network by simulating all the well-known wireless attacks against it to determine if unauthorized user can exploit the wireless network and get foothold on the internal network to perform further attacks.
The following represents some and part of the attacks that will be performed during this assessment:
- Evaluate and Cracking Authentication Protocols.
- Wireless Network Reconnaissance.
- Detect Hidden SSIDs.
- Installing Rough AP.
- Installing Evil Twin AP.
- Network Sniffing.
Attack Objectives
The following represents the objectives of this attack:
- Trying to get into the internal network by cracking WiFi network
- Assess the security level of the configured wireless network to verify if any unauthorized user can exploit it and gain foothold on the internal environment.
Looking for expert support in Red Teaming?
Fill in your details and our team will reach out to discuss your needs.